ERROR_GEN_FAILURE [code 0x0000001f] When Attempting to Join vCenter to Active Directory
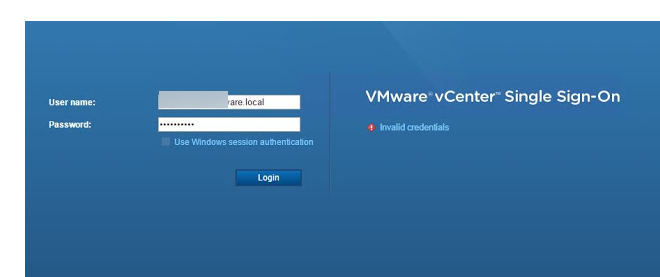
A common practice when installing VMware in an environment is to join vCenter to the domain. This not only enables not only users to log in to vSphere with their network credentials, but it is also used for Role-Based Access Control (RBAC) to various virtual machines within the environment. Imagine everything in your environment is running fine, then you start seeing other services such as backups failing or users reporting Single Sign-On authentication failures such as the one shown below:
When you attempt to login to the system, your own credentials fail, but you are able to login with the local vCenter administrator account. There are a number of troubleshooting steps to investigating this problem. The first would be to validate the integration between the VMware Platform Services Controller and Active Directory.
To do this, go to Home > Administration > Single Sign-On > Configuration and select the “Identity Sources” tab. Here, the domain is listed. Select the domain, edit, verify the settings, then save the configuration. However, in the process of saving the information, the following error is returned:
The "Join active directory" operation failed for the entity with the following error message.
The format of the specified computer name is invalid [domain.com]
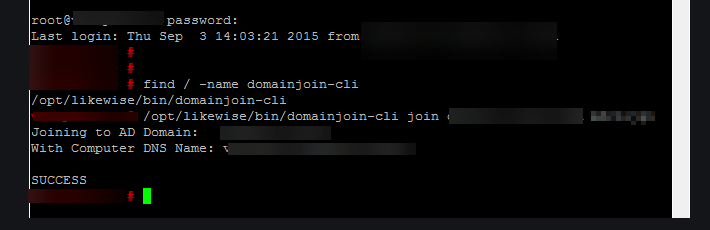
There is not a lot of information with this error. As in most cases, more information can be obtained from the command line. However, if you try the following step to reconnect vCenter to Active Directory, it will probably fail with a specific error code. To rejoin the appliance to the domain, locate the name of the Platform Services Controller in Active Directory, right-click, and select “Reset Computer Account”. Then, open and Putty session to the Platform Services Controller (PSC) and use the following command to attempt to rejoin the PSC to the domain.
/opt/likewise/bin/domainjoin-cli join [domain] [user name] [password]
error is returned:
The "Join active directory" operation failed for the entity with the following error message.
The format of the specified computer name is invalid [domain.com]
There is not a lot of information with this error. As in most cases, more information can be obtained from the command line. However, if you try the following step to reconnect vCenter to Active Directory, it will probably fail with a specific error code. To rejoin the appliance to the domain, locate the name of the Platform Services Controller in Active Directory, right-click, and select “Reset Computer Account”. Then, open and Putty session to the Platform Services Controller (PSC) and use the following command to attempt to rejoin the PSC to the domain.
/opt/likewise/bin/domainjoin-cli join [domain] [user name] [password]
At this point, the error returned is: ERROR_GEN_FAILURE [code 0x0000001f] When Attempting to Join vCenter to Active Directory. In researching this error, it turns out that by default, VMware utilizes SMBv1 when joining and synchronizing with Active Directory. Yes, most technology professionals are well aware of the security risk that SMBv1 imposes and would love to have it totally removed from the environment. The problem is that while this is disabled by default in Windows Server 2012 and above.
The reason it still exists in many environments is due to the existence of legacy Windows XP and Windows Server 2003 system. So, many administrators go back and enable the feature on the server operating system. From experience though, enabling SMBv1 on the domain controller does not resolve this issue. In the environment this article is based on, all of the domain controllers had been upgraded to Windows Server 2019, and the functional level of the forest and domain raised to 2012R2, with SMBv1 enabled, but the problem persisted. In order to join the PSC back to the domain, the following steps need to be followed:
- Ensure the computer account has been reset. This should have been done as part of the previous attempts to join the PSC to the domain
- A Putty session to the PSC logged in with the root account needs to be opened. Either enable SSH, or log into the console and switch to the shell using shell.set --enabled true followed by shell
- Enter the following commands to enable SMB2 on the system
-
/opt/likewise/bin/lwregshell set_value '[HKEY_THIS_MACHINE\Services\lwio\Parameters\Drivers\rdr]' Smb2Enabled 1 -
/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\lwio\Parameters\Drivers\rdr]' 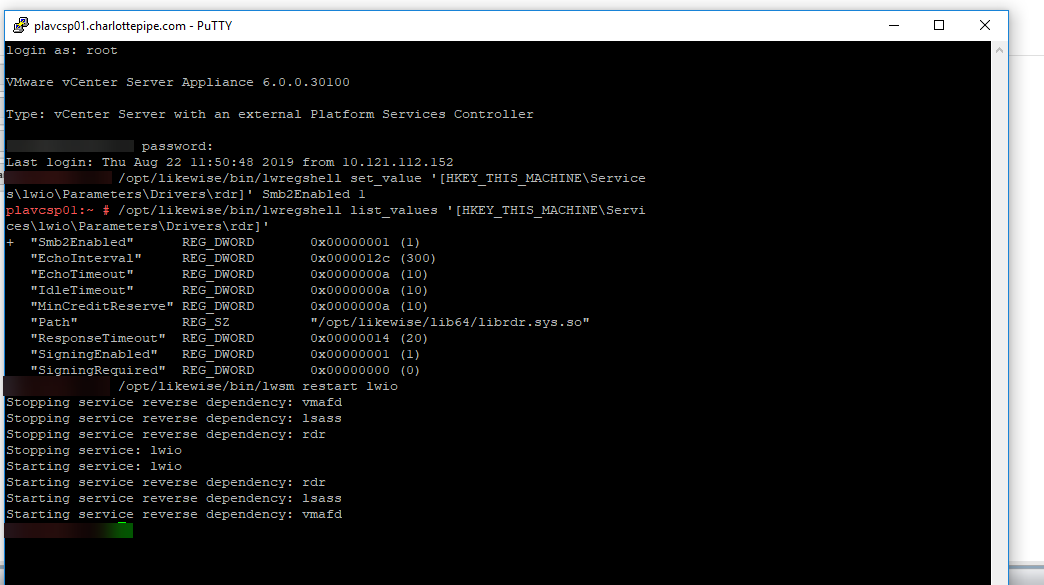 As you can see, SMB2 is now enabled, but the services need to be restarted. Use the command in the next step to restart the services.
As you can see, SMB2 is now enabled, but the services need to be restarted. Use the command in the next step to restart the services. -
/opt/likewise/bin/lwsm restart lwio
-
- After the services have restarted, run the command same command to join the PSC server to the domain
-
/opt/likewise/bin/domainjoin-cli join [domain] [user name] [password]
The command should now return a success response.
The final test is to now log in to the web interface with your AD credentials. Once that has been completed successfully, the system has been fully tested as now being AD integrated.
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)